“It’s one thing to do a great job; it’s quite another to make sure the customer sees it that way.”
The above quote is one I often issue when talking with folks. Those who know me might roll their eyes a bit because they’ve heard it so often.
But that doesn’t change the truth of it.
I’m of the opinion that no service provider should ever sell security services without a strategic and tactical management plan attached. It is the single best thing you can do to ensure the success of a client’s security program, giving them tangible results that translate to business outcomes.
With that said, if done wrong, it can lead to serve as a wedge, with the client coming to the opinion of: “What am I paying for?”
In this article, I’m going to give you 4 sections to use in your vCISO report, which provide a blueprint for delivering security services effectively – in a way that delights your clients and positions you as their primary trusted advisor.
Section 1
General Recap
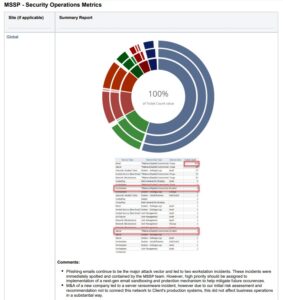
This section should always, always start with a single metric or trendline showing the current health of the security program. Your client wants to know: “How are we doing?” – and you’d better make that obscenely simple for them to digest.
Following that, of equal importance, use this section for the one-offs or adhoc items/questions/concerns that have popped up over the review period. This is a critical step to show the client that you’ve heard them, and have addressed or taken action on their queries. It’s basically active listening put into report form.
It’s important that you have a defined and processed system for gathering these from all the different touch points in your organization throughout the review period.
For Example: If a stakeholder mentioned they weren’t happy about the way something was handled, that should go in this section. A ticket should be opened up for internal review, and you should provide a status as to why it happened, what you’ve done to fix it, and an assurance that it won’t happen again.
That’s just one example, and this could be a wide variety of items, such as questions on reports, ideas or requests for simple items, etc.; bottom line is to show the client that you’re listening and taking action on the little things. It shows you’re attentive to their unique needs.
Use what I call my RCT task framework (Resource, Commitment, Time) to describe new takeaways from the convo. Do this for things that are the client’s responsibility as well. Then you’ll have a list of commitments from stakeholders on the call to iterate against over the upcoming review period.
Make sure you come with updated status for anything outstanding assigned to your organization, and then ask for status from any client responsibilities. Update with RCT accordingly. This is huge to build accountability loops in.
Section 2
Metrics Review
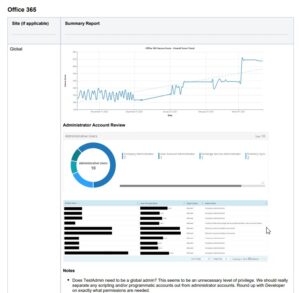
First things first – It’s a must that your reports pull data from your tools automatically. Your vCISOs should not be spending their time manually going to different systems and putting this data together.
Their time should be spent interpreting the report – if you haven’t automated report creation, your team will be in a world of hurt, and profitability and CSAT will suffer.
Now let’s start with what Metrics Review isn’t. This isn’t a time for you to just export and read statistics from a dashboard or report. The client wants you to help them cut through the noise, and help them understand any actionable items from those reports.
What this is: This is a time for you to *interpret* the metrics for the client. Have “stories” with actionable outcomes ready.
-
- Going over MTTD/MTTR results – review response times and identify any anomalies. Look into those and see *why* there were anomalies. Be ready with the reasons and associated actions – e.g. due to improperly classified alert, talked to SOC, they’ve made adjustment on this.
- Alert types and/or baselines – spike of brute force attempts in M365 – Looks scary, client wants to know “Are we ok?”
- Have these answers ready ahead of time – e.g. we talked to the SOC, this was most likely due to actor X running a campaign. We’ve seen this in our other clients too; SOC verified no compromises and everything is fine – recommend sending out a memo to your people to stay vigilant just as a reminder. I have a template you can use.
The bottom line here is EQ.
-
- Don’t burden your vCISO teams with long and arduous report processes. I’ve heard of upwards of 10+ hours in some situations to put a report together – that’s simply untenable.
- Put yourself in the client’s shoes. They don’t care about the technology as much. They want the TL;DR version. Are you doing your job; and are they secure? Review the reports in that light, and be proactively prepared to answer those items with an easy to understand story.
Section 3
Strategic Review
Finally! We’re actually doing some strategy work!
An actionable strategic roadmap and the tactical execution of it is at the heart of an effective vCISO program. It is a must that you use my RCT (Resource, Commitment, Time) framework to manage these tasks.
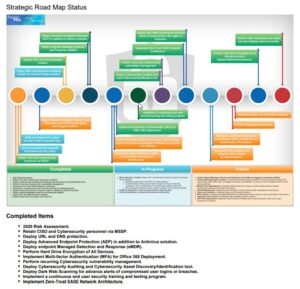
A road map is the heart of your program, and as such, it must be the MOST streamlined and automated part of the program. The strategic roadmap should be the culmination of your risk assessment process.
-
- Risk Assessment feeds into Gap Analysis
- Gap Analysis uses *exact* language for recommendations
- Exact language corresponds to controls matrix
- Controls matrix and language is plugged into Strategic Roadmap
- Strategic Roadmap is organized and prioritized by vCISO with business stakeholders, and executed against.
Consider the following workflow:
1) Risk Assessment finds delinquencies in:
-
- Deploy Vuln Management Program
- Deploy EDR Solution for Endpoints
- Develop and Implement Formal Incident Response Policy
3) Controls Matrix has mapping for those recommendations to services/tools
4) Strategic Roadmap lists priority for Gaps/Recommendations to be implemented
-
- It’s agreed upon by all stakeholders and is the ultimate source of truth for tactical execution!
Work in Progress (WIP)
At this point, we need to stop and talk about WIP (Work in Progress).
Manage your WIP properly! If you don’t marshal your teams and resources effectively, it’s a sure way to cause chaos and additional problems as things spin out of control.
-
- If you haven’t already, read “The Phoenix Project” and the “The Goal” for some timeless techniques on how to effectively manage work.
- Using a Kanban board approach here is a great technique, but however you do it, make sure you are managing WIP (Work in Progress) effectively. You don’t want too many balls up in the air.
- Don’t get too tied to the plan, it will inevitably change as risk and priorities of the business adjust to the current landscape. Be flexible, be a partner, and be ok with moving priorities around. This is were a well-developed WIP approach helps. “Ok, we can work on that, but which of these other things should we pause?”
Section 4
Future Intiatives
I can’t stress enough how important this section is. This is where you help the client plan, and perform possibly your most important function as trusted advisor.
-
- It’s highly important to make sure you are tuned in to what the client is mentioning here. The “Future” section is your safety net, and the final line of defense in a closed-loop communication system. We know we can’t do everything at once, and we have limited time – so we have to make the best use of it.
- This is where you prevent things from falling through the cracks, and also, where you continue to “fill the hopper” to keep a steady supply of “do-next” items so that momentum isn’t lost.
- You must communicate with your Account Management teams on these. Don’t let your org be the bottleneck here. If new items are identified, make sure you have takeaways using my RCT framework to identify vendors, get quotes together, and be ready to execute the instant the client says go!
There are two primary focuses that round this section out:
-
- The items from the roadmap that are queued up, due to the priority/capacity calculations we’ve performed in previous steps.
- Items that are uncovered or talked about as concerns with the client over the course of risk, regulatory, operational, or other discussions.
Consider the following: During general review and discussion, it comes to light that the client is considering going for their SOC2 Type 2 to help win more business with bigger clients.
You need to note it in the future section as an objective, with the RCT indicated for your org’s takeaways to either put a quote together, bring in some competitive quotes (if you don’t do it in house), and any other risk/cost needs to bring the client to a place where they can make an easy decision on this.
“Wait, did you just mention sales – the five letter dirty word?! We are consultants, we don’t hock products to our clients!”
-
- I’m here to tell you that as a vCISO, you are a little bit of everything. In this article, we’ve uncovered how you are a PM, scrum master, productivity expert, secretary, and many others. That includes account management.
- You are not “hocking products” – you are providing vetted and trusted services to help your clients achieve their goals – and that includes consultative selling. This is ethical, and clients appreciate someone who can be their guide and trusted advisor to help them make decisions that they would otherwise have to make in a black box fashion.
Conclusion
I hope this article was helpful as you consider launching or improving your security program. I don’t want to sugarcoat it – there are a wide range of considerations to account for, and it takes skill to deliver vCISO services effectively.
However, using this framework is the best way I’ve found to bind all the pieces into a cohesive, compelling narrative that speaks to your client, allowing you to make the leap to becoming a holistic solution provider.
If you’d like to explore how PowerPSA can help you design, train for, and launch an effective security offering (including vCISO services), or if you want to use our turnkey vCISO channel program to augment your current stack, please reach out by clicking the chat icon, and Unleash the Power of Your MSP!
-
- Vuln Management
- Malware Control
- Incident Response
2) Gap/Recommendations should say:
-
- Deploy Vuln Management Program
- Deploy EDR Solution for Endpoints
- Develop and Implement Formal Incident Response Policy
3) Controls Matrix has mapping for those recommendations to services/tools
4) Strategic Roadmap lists priority for Gaps/Recommendations to be implemented
-
- It’s agreed upon by all stakeholders and is the ultimate source of truth for tactical execution!
Work in Progress (WIP)
At this point, we need to stop and talk about WIP (Work in Progress).
Manage your WIP properly! If you don’t marshal your teams and resources effectively, it’s a sure way to cause chaos and additional problems as things spin out of control.
-
- If you haven’t already, read “The Phoenix Project” and the “The Goal” for some timeless techniques on how to effectively manage work.
- Using a Kanban board approach here is a great technique, but however you do it, make sure you are managing WIP (Work in Progress) effectively. You don’t want too many balls up in the air.
- Don’t get too tied to the plan, it will inevitably change as risk and priorities of the business adjust to the current landscape. Be flexible, be a partner, and be ok with moving priorities around. This is were a well-developed WIP approach helps. “Ok, we can work on that, but which of these other things should we pause?”
Section 4
Future Intiatives
I can’t stress enough how important this section is. This is where you help the client plan, and perform possibly your most important function as trusted advisor.
-
- It’s highly important to make sure you are tuned in to what the client is mentioning here. The “Future” section is your safety net, and the final line of defense in a closed-loop communication system. We know we can’t do everything at once, and we have limited time – so we have to make the best use of it.
- This is where you prevent things from falling through the cracks, and also, where you continue to “fill the hopper” to keep a steady supply of “do-next” items so that momentum isn’t lost.
- You must communicate with your Account Management teams on these. Don’t let your org be the bottleneck here. If new items are identified, make sure you have takeaways using my RCT framework to identify vendors, get quotes together, and be ready to execute the instant the client says go!
There are two primary focuses that round this section out:
-
- The items from the roadmap that are queued up, due to the priority/capacity calculations we’ve performed in previous steps.
- Items that are uncovered or talked about as concerns with the client over the course of risk, regulatory, operational, or other discussions.
Consider the following: During general review and discussion, it comes to light that the client is considering going for their SOC2 Type 2 to help win more business with bigger clients.
You need to note it in the future section as an objective, with the RCT indicated for your org’s takeaways to either put a quote together, bring in some competitive quotes (if you don’t do it in house), and any other risk/cost needs to bring the client to a place where they can make an easy decision on this.
“Wait, did you just mention sales – the five letter dirty word?! We are consultants, we don’t hock products to our clients!”
-
- I’m here to tell you that as a vCISO, you are a little bit of everything. In this article, we’ve uncovered how you are a PM, scrum master, productivity expert, secretary, and many others. That includes account management.
- You are not “hocking products” – you are providing vetted and trusted services to help your clients achieve their goals – and that includes consultative selling. This is ethical, and clients appreciate someone who can be their guide and trusted advisor to help them make decisions that they would otherwise have to make in a black box fashion.
Conclusion
I hope this article was helpful as you consider launching or improving your security program. I don’t want to sugarcoat it – there are a wide range of considerations to account for, and it takes skill to deliver vCISO services effectively.
However, using this framework is the best way I’ve found to bind all the pieces into a cohesive, compelling narrative that speaks to your client, allowing you to make the leap to becoming a holistic solution provider.
If you’d like to explore how PowerPSA can help you design, train for, and launch an effective security offering (including vCISO services), or if you want to use our turnkey vCISO channel program to augment your current stack, please reach out by clicking the chat icon, and Unleash the Power of Your MSP!